PENTING :
Beberapa ide masih sangat sederhana. Mohon ide proyek di atas dikombinasikan dengan ide proyek yang lain sehingga cukup kompleks untuk dijadikan PA. Ambil minimal tiga judul dan jadikan judul yang lebih kompleks. Ide mengenai cloud masih dirancang, insya Allah akan diupdate dalam waktu dekat.
Title: STP Vulnerabilities, attacks and mitigation
Abstract:
The projects understand the internal architecture of STP packets and the fields inside it. The mechanism which attackers use to exploit the vulnerabilities in the STP packets is understood. The project understand the different features available on Cisco switches like BPDU-Root guard, Root guard , Loop guard along with appropriate configurations.
Title: Resolving Active FTP issues with Cisco CBAC
Abstract:
The users in an organization access internet through a normal firewall. Since a firewall is setup, the users are unable to access Active FTP servers on the internet. The project aims to setup a Cisco IOS firewall to resolve the issue. The generic issues with firewalls and Active FTP servers and how the CBAC feature on the Cisco IOS firewall resolves the issue.
Title: Mac-address authentication vulnerability on 802.11 wirelesses LAN
Abstract:
Mac-address authentication is a feature available on Cisco access points for authenticating wireless clients based on their mac-addresses.The projects aims to understand the vulnerabilities in this feature by exploring mac-spoofing attacks and how it can be used to defeat mac-address authentication.
Title: Defeating route table poisoning with OSPF
Abstract:
RIP v1 is an insecure protocol. It does not have an authentication support inbuilt. An attacker can craft invalid RIP packets and send it out on a RIP network. The RIP router would accept the same and update its routing table. This poisons the route table as invalid route entries are injected in the table. The project aims to understand how OSPF which has authentication inbuilt can be used as protection against the attack.
Title: Defeating cam flooding attacks with port-security
Abstract:
Cam flooding attack works by generating a large number of frames on a switch port and making the cam table of the switch to overflow, eventually making the switch to broadcast out received frames on all ports. The projects understands how portsecurity feature can be used to limit the number of allowed mac-address on a switch port to prevent cam flooding attack along with the actual configuration.
Title: Study on NAT flavors on Cisco routers
Abstract:
The aim of the project is to understand the different flavors of NAT on Cisco routers like Static NAT, Dynamic NAT and PAT. The use of these features in a real time environment and the configuration required to setup the features on the routers is understood.
Title: Cisco IOS Firewall IDS signatures.
Abstract:
Cisco IOS firewall has inbuilt intrusion detection signatures. The aim of the project is to understand the different types of inbuilt IDS signatures and the types of attacks and packets which would trigger the signatures. The different tools which attackers use and the methodology to conduct the attacks or crafting malformed packets is explored.
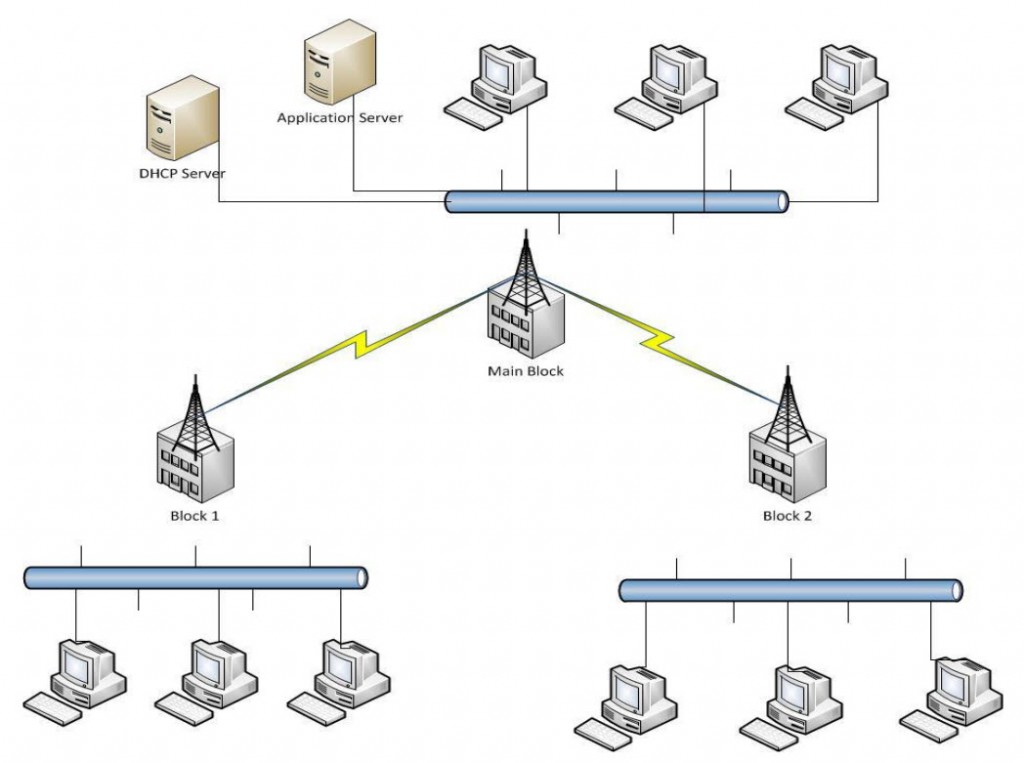
Title: Wireless VLAN design in Campus
Abstract:
A wireless network has to be setup in a campus which has 3 blocks. There are three departments in the campus namely Management, faculty and students. There are approximately 30 users each in each department. Each department is separated as different vlans, vlan 2, vlan 3 and vlan 4. Each of the vlans are configured are mapped with the network address 192.168.1.0/24, 192.168.2.0/24 and 192.168.3.0/24. Wireless access is required at the different blocks for which access points are installed. A DSL internet connection is available which is to be shared by all the users on the network. The campus plans to use a Cisco and Microsoft infrastructure. The design strategy and methods by which multiple vlans can be hosted on an access point , which would provide dhcp addresses from a windows dhcp server needs, switches and routers with appropriate configurations to be identified. The users should also be able to access internet after successful connection.
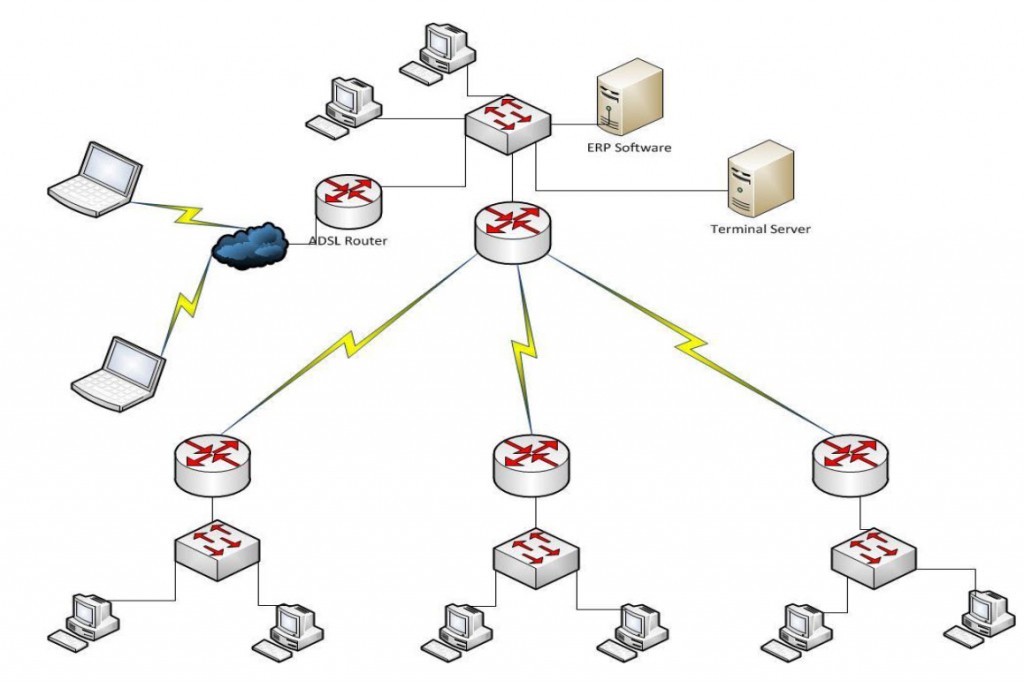
Title: Multi Site MPLS network design
Abstract:
An organization has 4 locations, 1 main location with 3 branch location. The user in the branch location needs to access an ERP server in the main location through the MPLS network. Mobile users should be able to access the ERP server through the terminal server using the ADSL internet connection setup the main location. Cisco MPLS routers are proposed for the connectivity. The network should be designed with appropriate network addresses for different locations, the configuration required on the terminal server, ADSL router for remote access.
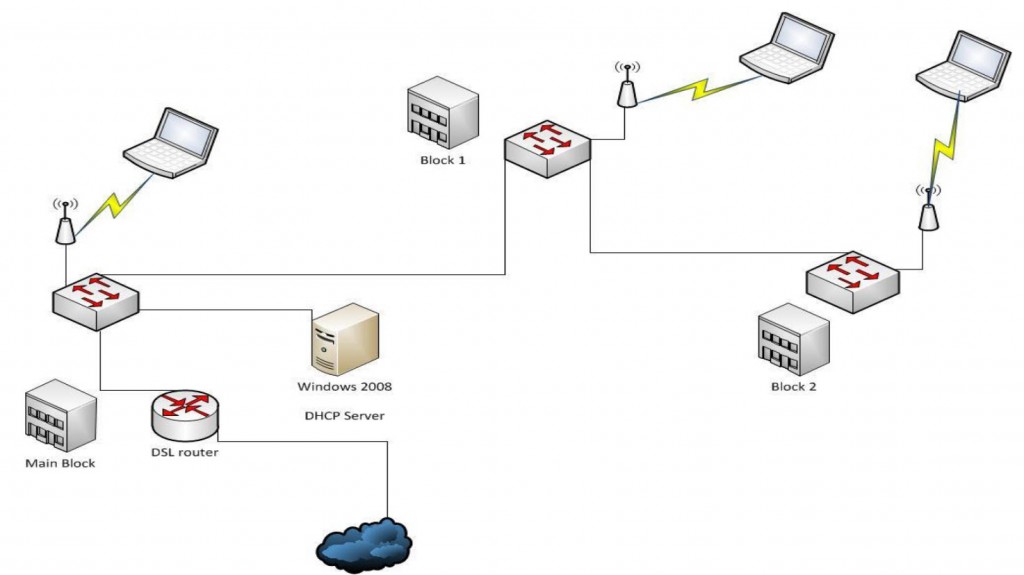
Title: Wireless Multi Site campus network design
Abstract:
In a university campus, there are three blocks, main block, block 1 and block 2. The distance between Main block and block 1 is 200 mtrs and between main block and block 2 is 300 mtrs. There is a clear line of sight between the blocks. There are 30 computers in the main block with an application server. There are 20 and 10 users in block 1 and block 2 respectively. It is required to link up the sites with Cisco wireless access points and appropriate antenna. The network design strategy, with network addresses, dhcp identification and configuration for users to receive dynamic ip addresses and for users on block 1 and block 2 to access the application server at the main block needs to be identified.
Title: Rogue DHCP server detection tool
Abstract: The project develops a tool for identifying rogue DHCP servers on the network. The tool returns the list of DHCP servers on the network, from which the rogue DHCP server can be identified. The tool is developed with Scapy and Python.
Title: TCP port scanner
Abstract:
The project develops a tool which is used for identifying TCP based applications running on a server. The tool returns the port numbers which are open on the server along with the corresponding application name. The tool is developed with Python and Scapy.
Title: Access control list testing tool
Abstract:
Access control list is a security feature which is available on routers, switches and firewalls which permits or denies packets based on IP and TCP/UDP port numbers. The projects aims to develop a tool which can simulate custom IP and TCP/UDP packets based on user input for testing. The tool is developed with Python and Scapy.
Title: VLAN max limit testing tool for Cisco switch.
Abstract:
The project develops a tool which would test the maximum number of vlans on a Cisco switch. For this purpose, the max number of vlans supported on the switch platform is understood from the technical specification. Once the max number is identified, the tool is executed from a remote PC, connects automatically to the switch using telnet and creates the specified number of vlans on the switch. The tool is developed with TCL/TK.
Title: IP Scanner tool for a network.
Abstract:
In a DHCP network, it is difficult to identify unused IP addresses on the network. The project develops a tool which is used for listing unused IP addresses on the network. The tool is executed from a computer on the network. Scapy and Python is used to develop the tool.
Title: Spanning tree election testing tool for switches.
Abstract:
The spanning tree protocol is used on a switch topology to prevent loops. Spanning tree protocol uses an election process, where the switch which has a lower priority value in the BPDU is elected as the root bridge. The project develops a tool which would develop custom STP packets to generate STP packets with the required priority value.
Title: ICMP Message testing tool
Abstract:
ICMP messages are used for specific purpose. Based on ICMP message type and code sent from the initiator, the destination would respond correspondingly. To test the functionality of ICMP, a tool is created which can craft custom ICMP packets. The tool can take ICMP code and type as a user input and is developed with Python and Scapy.
Title: IP spoofing attack tool
Abstract:
In IP spoofing attack, the attacker uses custom IP address values in the source address field of the IP packet. The project develops a tool which would create custom IP packets with user input as source address and the number of times the packet has to be sent on the network. The tool is created with Python and Scapy.
Title: URL Filtering testing tool
Abstract:
URL filtering is a feature which is available on routers and firewalls. The feature blocks access to a website based on the URL information. The project develops a tool which can be used to create custom URL information, which is taken as a user input. The tool is developed with Python.
Title: Web server finger printing tool
Abstract:
Web server finger printing is method by which the operating system and version of the Web server is identified. The project develops a tool which would finger print the web server and return the information to the user. The tool is developed with Python and Scapy.
Title: LAN speed tester tool Abstract:
The project develops a tool to identify the time it takes for a packet to flow between two computers on a LAN network. ICMP protocol is used for the purpose. The tool is developed with Python and Scapy.
Title: DDOS based TCP Syn flood attack tool
Abstract:
TCP Syn flooding is an attack which is based on TCP based servers. When the attack is generated from different random source IP addresses, it is termed as DDOS attack. The project aims to develop a tool by using the Hping frame work to simulate the attack.
Title: URL to IP mapper tool
Abstract:
The project develops a tool which would return the IP address of a URL. The tool takes the URL as a user input and provides the IP address which is mapped with the URL. The tool is developed with Python and Scapy.
Title: IP Packet TTL manipulator tool
Abstract: The project develops a tool which can be used for crafting custom IP packets with the required TTL value. The TTL value is taken as a user input. The tool is developed with Python and Scapy.
Title: Back door scanner tool
Abstract:
Back door is a mechanism by which an attacker can gain access to a remote computer. Back doors are possible when computers have applications like VNC, Remote desktop running on the target without password authentication. The project develops a tool which would scan a computer for back door applications and return the list of available applications. The project is developed with Python and Scapy.
Title: Remote access scanner tool
Abstract:
Remote access is the mechanism by which devices can be accessed remotely using applications like Telnet, SSH, FTP, HTTP etc. The project understands the different types of remote access protocols and develops a tool which would scan a remote device for the list of available protocols. The tool is developed with Python and Scapy.
Title: Mac-spoofer tool
Abstract:
Mac-spoofing is the mechanism by which an attacker uses a different mac-address. The project develops a tool which would take the value of the source mac-address as input from the user. The tool can be used to generate custom ethernet frames with the required source mac-address. The tool is developed with Python and Scapy.
Title: VLAN packet crafter
Abstract:
The project develops a tool which would generate custom 802.1Q vlan packets. The tool takes the required vlan id as input and transmits on the network. The tool is developed with the Python and Scapy.
Title: Router banner grabbing tool
Abstract:
Banner grabbing is the process by which the operating system and version running on a system is identified. The project develops a tool which would perform banner grabbing operation on a Cisco router. The tool is developed with Python and Scapy.
Title: IP/MAC Enumerator tool
Abstract:
The project develops a tool which enumerates the list of IP and Mac-addresses on the network. The tool is executed from a computer on the network. The tool is developed using the Nmap framework.
Title: ARP cache poison tool
Abstract:
ARP cache poisoning is an attack by which the attacker poisons the ARP cache of a remote system. The project develops a tool which would generate custom ARP packets for the purpose of ARP cache poisoning. The tool is developed using Python and Scapy.
Title: DNS server scanner tool
Abstract:
The project develops a tool which would scan the list of available DNS servers on a LAN network along with the IP address of the DNS servers. The tool is developed with Python and Scapy.
Title: HTTP Packet crafter tool
Abstract:
The project develops a HTTP packet crafter tool which would simulate custom HTTP packets on the network. The tool is developed with Python.
Title: Reverse DNS tool
Abstract:
Reverse DNS is the process by which the domain name corresponding to an IP address is retrieved. The project develops a tool which would take the IP address as the user input and display the domain name. The project is developed with Python and Scapy.
PENTING :
Beberapa ide masih sangat sederhana. Mohon ide proyek di atas dikombinasikan dengan ide proyek yang lain sehingga cukup kompleks untuk dijadikan PA. Ambil minimal tiga judul dan jadikan judul yang lebih kompleks.
Ide untuk Cloud :
Membangun Interface Gaming Cloud berbasis GamingAnywhere
Membangun Life casting cloud berbasis GamingAnywhere
Membangun VOD cloud berbasis Gaming Anywhere
Membangun toko aplikasi game android berbasis GamingAnywhere
web :
http://gaminganywhere.org/index.html
2 responses to “Ide Proyek Akhir untuk Network Engineering dan Network Programming”
I see many websites outrank your site in google’s search results.
You should build more contextual backlinks. These type of backlinks are the most powerful after all
these google algorithm updates. I know writing content is
hard work, but i know what can help you save a lot of time, search in google for:
Jyengmos’s Rewriter
Found your post on Google, the headline caught my eye and it was a good read.